The Single Strategy To Use For Risk Management Enterprise
Table of ContentsThe 5-Minute Rule for Risk Management EnterpriseThe Facts About Risk Management Enterprise UncoveredRisk Management Enterprise Fundamentals Explained
Control that can watch or modify these elements by establishing specific access rights for private users, making sure information safety and security and tailored use. Allows customers to tailor their interface by picking and arranging crucial data elements. Supplies a customized experience by enabling modification of where and exactly how information components are presented.It enables accessibility to real-time incorporated data promptly. Facilities can utilize comprehensive data intelligence for quicker and extra educated decision-making.
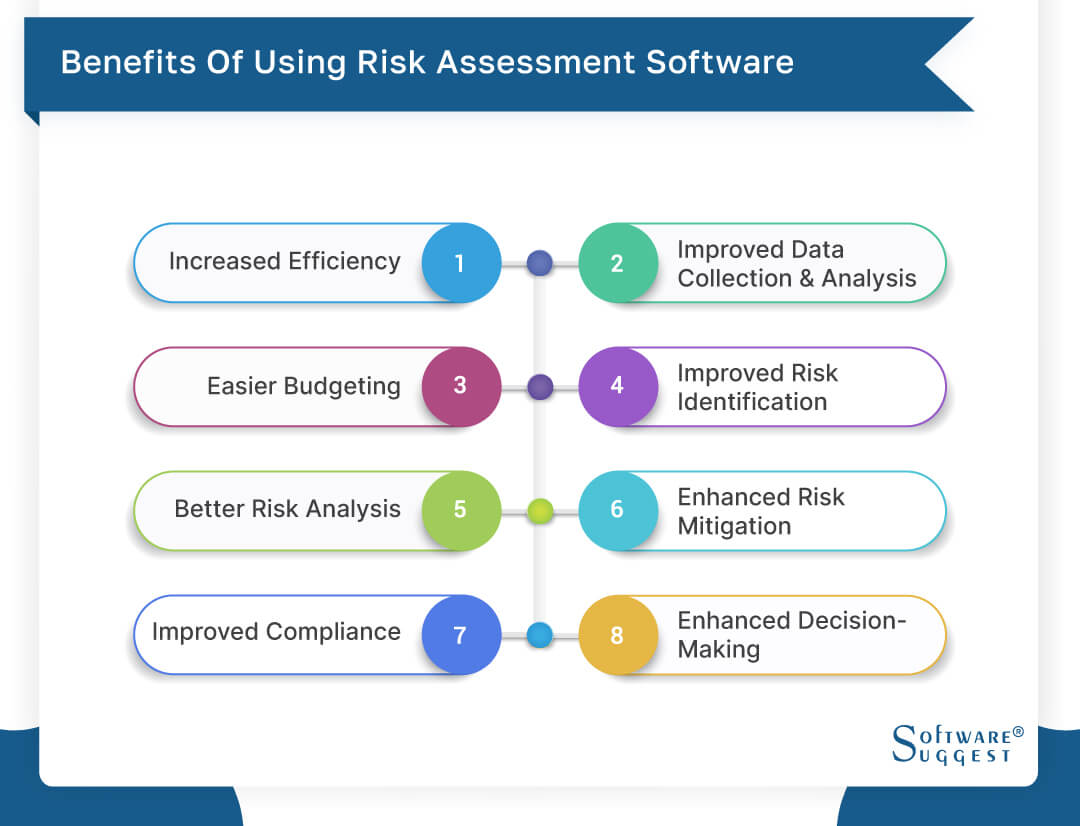
Diligent is a threat administration software that enables enhancing performance, and boosts development. It likewise helps keep an eye on dangers with ERM software application that includes incorporated analytics and adapts to your service requirements.
The smart Trick of Risk Management Enterprise That Nobody is Discussing
Streamlines the procedure of collecting danger data from numerous components of the organization. Gives management and the board with real-time risk insights. Usage ACL's innovative analytics to detect risk patterns and predict dangers.
This permits companies to capture risk insights and red flags in the third-party vendor's protection record. This enables for saving risk evaluations as auditable records. It also enables exporting them as PDFs. To complete the process business can complete a review day. Enables firms to capture and document danger understandings redirected here and warnings in third-party vendor safety reports.
It additionally lowers danger with structured conformity and risk management. It can assist gather and track all your risks in the Hyperproof risk register.
It supplies fast access to necessary info and documentation. This guarantees the protection of Active proof circumstances by allowing multi-factor verification (MFA) making use of authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
Risk Management Enterprise Can Be Fun For Everyone
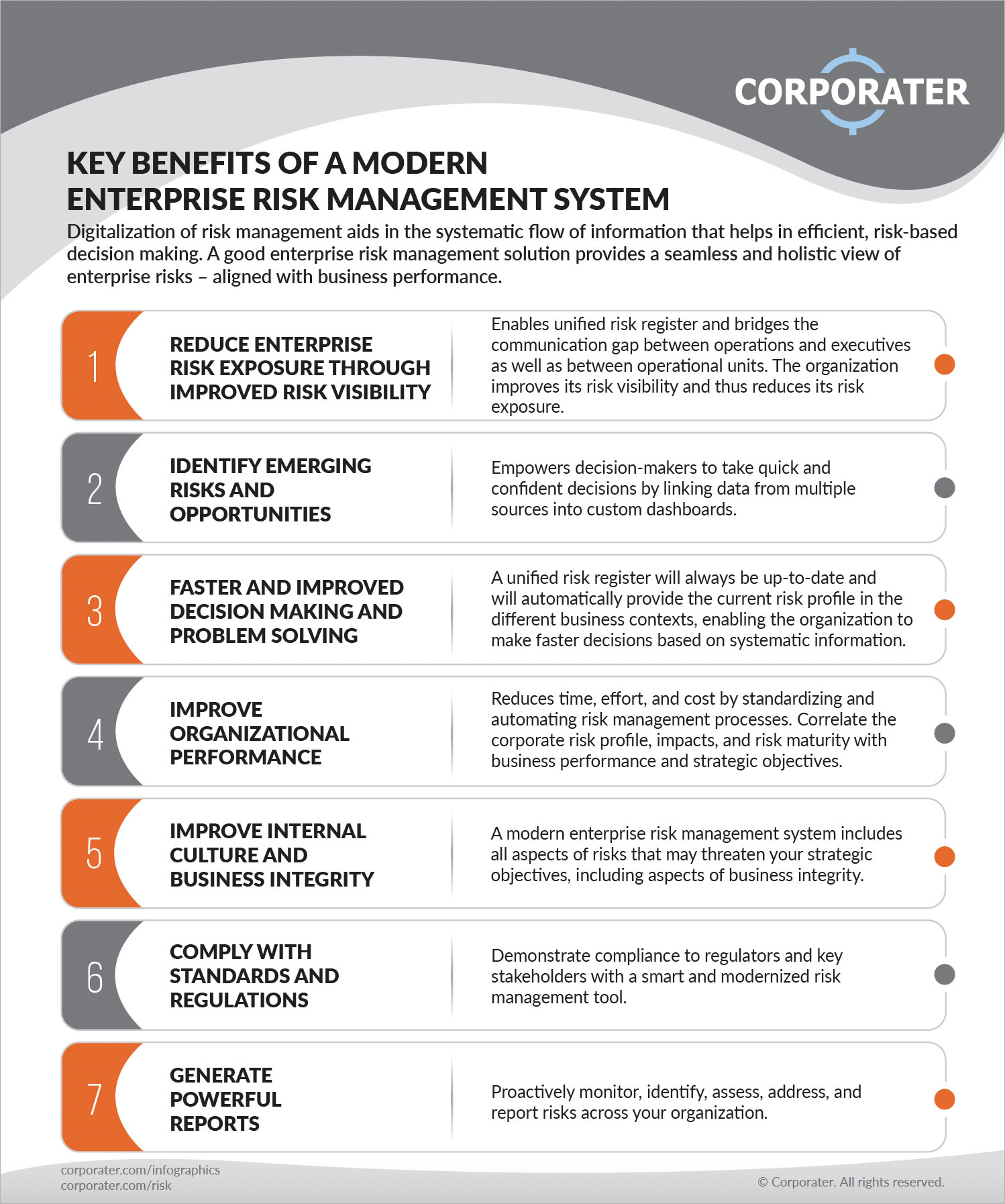
It enables smooth process and integrations and minimizes inefficiencies. It provides top-tier safety and security functions to Our site secure sensitive a knockout post information. This risk monitoring software application is a perfect tool for centers aiming to repair unneeded problems or threats. It includes several sorts of features that make it particular for ERM supervisors. Below we have actually highlighted a few of its vital features for your advantage, so have a look.
Users can also utilize the AI-powered devices and pre-existing content to produce, assess, focus on, and address risks successfully. Streamlines the process of configuring and occupying risk signs up.